Cybersecurity services
One-stop solution for your Security Requirements
An intelligent cyber partner to enhance your security posture by improving the core security.

Services We Offer
Managed Detection & Response
With the power of AI and human expertise, we detect, analyse, and respond to threats proactively to provide cohesive defense and central monitoring.
Threat & Vulnerability management
We Identify, classify remediate, and mitigate high-risk areas through an iterative process to secure the crown jewels of the organization.
Governance Risk & Compliance
Our tailored solutions establish, manage and attain a mature state of Enterprise GRC for achieving strategic business objectives & Goals of an organization.
Data Protection & Privacy
Deliver trusted experience to customers by securing the privacy, availability, and integrity of their data with a holistic and adaptive approach.
IoT/OT Security
Continuous advancement of IoT/OT security posture will enhance the visibility, security, and monitoring of the threat and vulnerability landscape.
Security Implementation Service
A powerful cybersecurity servies implementation to safeguard your assets from evolving digital threats.
Our Mission
We provide 360˚ cybersecurity service offerings tailored-made to meet customers' requirements. We adopt an AI security approach to achieve a proactive state of cyber maturity & resiliency.
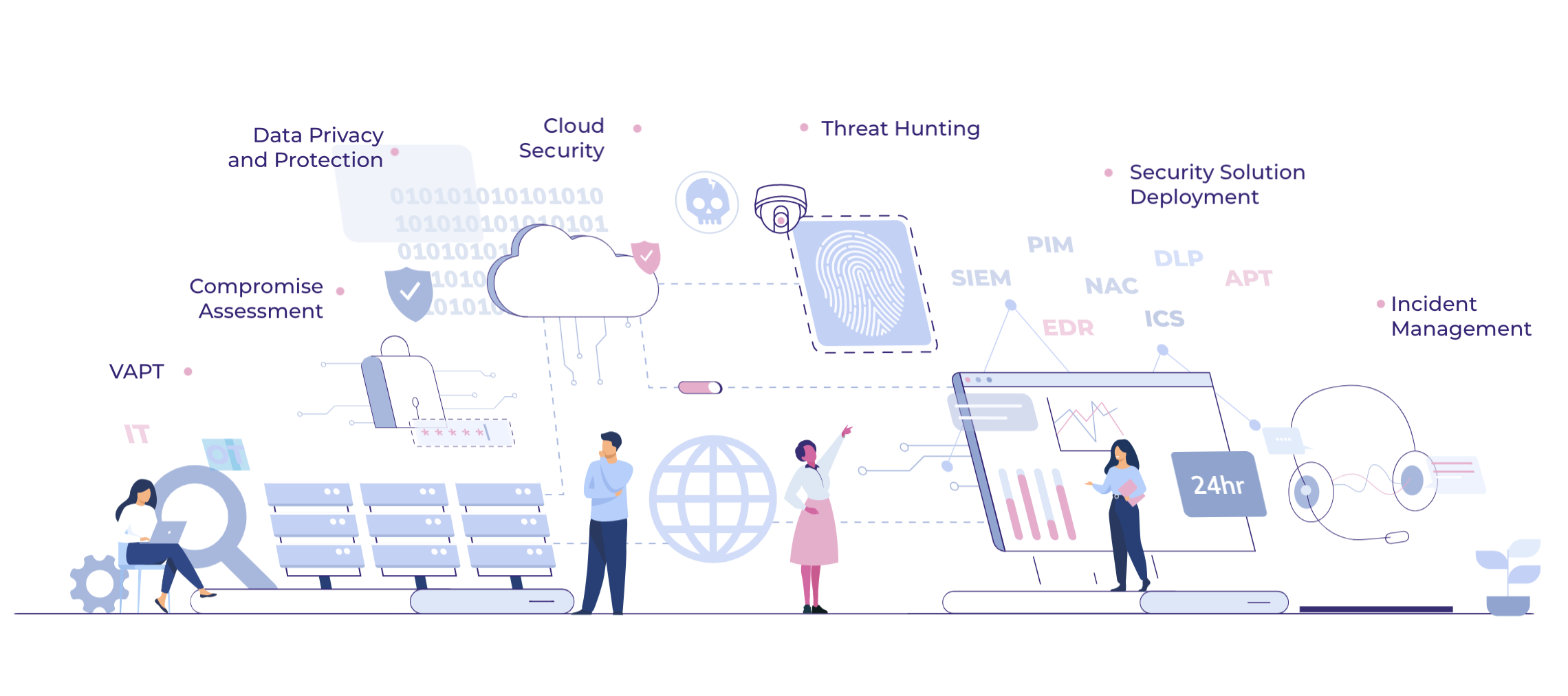
Our Security Capabilities
Our Approach
Our threat detection methodology aligns with the cyber kill chain framework and strictly follows the industry standards like ISO 27001, ISO 27701, NIST, PCI-DSS, and SOC 2 Type II.
Questions
What Cyber security services do we offer?
We offer Information and Cyber security strategy & consulting services that help you define the appropriate framework. We offer a range of services, including the following, to protect your business from threats and strengthen your cyber defences.
What are the three fundamental principles of cyber security?
Confidentiality, Integrity, and Availability are the three guiding cyber security fundamentals principles that underpin all discussions about security, including cyber security. Depending on your individual needs, we will assist you in adapting by customizing these beneficial guiding principles.
What are the cyber security dos and don'ts?
The strongest defence against cyber security attacks is preparation. A little prevention will save you a lot of headaches and money in the long run:
What are the biggest issues with cyber security?
These cyber security dangers need extra attention from your company:
What should a cyber security policy include?
The cyber security policy should include:
-
- Introduction
- Purpose statement
- Scope
- List of confidential data
- Device security measures for the company and personal use
- Email security
- Data transfer measures
- Disciplinary action
What are Cyber Security Interview Questions?
-
- What is encryption?
- What is the difference between Symmetric and Asymmetric encryption?
- What is the difference between IDS and IPS?
- What does the CIA triad mean?
- How is Encryption different from Hashing?
- Why is a firewall used? What does it do?
- What is the difference between Vulnerability Assessment(VA) and Penetration Testing(PT)?
- What is a three-way handshake?
- What are the possible response codes for a web application?
- Describe traceroute. Why is it employed?
What should I ask about cyber security?
Your board should focus on the following key cyber security questions:
-
- Do we know the necessary knowledge to manage cyber risks?
- How well does our cyber security plan mitigate company risks?
- How can we safeguard the private data handled and kept by third-party vendors?
- Do we have cyber insurance?
- Do we employ the proper data governance approach to reduce cyber risk?
- How do we keep up with the state of the cyber threat landscape?
- Do we have a tested response strategy for cyberattacks?
- How can we recognize cyber-attacks and react to them?
What are the seven layers of security?
When discussing the seven cybersecurity layers, you should concentrate on the important data that you are trying to secure.
-
- Mission Critical Assets
- Data Security
- Application Security
- Endpoint Security
- Network Security
- Perimeter Security
- The Human layer
What are the stages of an attack?
-
- Survey:Investigating and analyzing available information about the target to identify potential treats & vulnerabilities.
- Delivery:Reaching a point in that system that exploits vulnerabilities easily.
- Breach:Exploiting the vulnerabilities to gain some form of unauthorized access.
- Affect:Conducting activities within a system that achieve the attacker’s goal.
What are the Un-targeted cyber attacks?
-
- Phishing:It is a practice of sending emails to a large group of recipients that request private information (such as bank account numbers) or direct them to a fraudulent website.
- Water holing:It is a practice of setting up a fake website or compromising a legitimate one to exploit visiting users.
- Ransomware:The attacks include spreading software that encrypts files and demands a ransom.
- Scanning:It is a practice of attacking broad swathes of the Internet at random.
What are the different types of Targeted cyber attacks?
-
- Spear-phishing:Sending emails to specific recipients that could include a malicious attachment or a link to a malicious website.
- Bot-net Deployment:DDOS (Distributed Denial of Service) attack on a system.
- Subverting the supply chain:Attack the software or equipment being delivered to the company.
What exactly do we as a cyber security firm do?
- Let’s take a quick look at how we approach:
- Evaluate and identify top risks, risk appetite, access controls, and vulnerabilities.
- Treat and analyze risks as per the company threat landscape and treat those to improve security posture.
- Continuous tracking and monitoring of cyber risks, treatment strategy, and remediation.
- With our 360-degree solution, we pride ourselves on delivering optimal value to your business:
- enhanced user experience to instantly make necessary software available. The use of reclaimed licenses can also lower true-up expenses associated with licensing.
- Assist in educating users and reducing support load on Service Desk through lesser calls.
- Improve TAT for integrating test beds and faster testing cycles with better remote integration.
- Eliminate numerous firewall rules to improve developer efficiency and increase security.
- Self Service and faster TAT to Dev Teams to manage their platforms for Dev and Test phases of SDLC.
- Drastically reduce wastage of paper by reduction of un-collected prints at the printing bay.
What is the objective of cyber security?
- The objective of cyber essentials is that you are aware of the risks to your business, have them documented, and have a plan in place to address them. This can drastically lower the cost and limit the impact of a cyber-attack on your company.
What skills are required for cyber security?
- Here are the ten areas where skills are most in-demand in recent years:
- Risk identification and management
- Technical fundamentals
- Data management and analysis
- DevSecOps
- Cloud
- Automation
- Threat hunting
- Interpersonal skills
- Business acumen
- Agility
Which is best, AI or cyber security?
- We can say that AI is becoming an integral part of cyber security in many ways. Some algorithms and procedures that can be implemented at various levels and capacities can improve the efficiency of your organization’s security and save your security team’s time for other crucial tasks
Is cyber security in demand?
With businesses gradually digitizing their products and the tendency to work remotely from around the world becoming more familiar, maintaining secure information and data systems is and will always be needed. Overall, the demand for cyber security assessment is booming.
Doesn’t everyone already know about cyber security?
Although people are aware of the basics of cyber security, they are not sufficiently protected. The majority of individuals may be aware of the problem and make an effort to protect their data, but the reality is cyber threats are getting worse. However, cyber security applies to IT organizations/enterprises and the individuals who are employed by the organizations. Training and mock drills can help combat high-impact as well as accidental or unintentional cyberattacks.
What are the primary cyber security services we provide?
Threat and Vulnerability Management, Managed Detection and Response, Application Security, Network Security, Cloud Security, and IoT/OT Security.
What are EDR (Endpoint Detection and Response) Solutions?
Endpoint Detection and Response Solutions (EDR) are defined as solutions that capture and store endpoint-system-level behaviors, employ a variety of data analytics techniques to identify suspicious system behavior, offer contextual data, thwart malicious activity, and offer recommendations for remediation to restore.
What is the difference between MDR, XDR, and EDR?
Managed detection and response are referred to as MDR, Extended detection and response are referred to as XDR, and Endpoint Detection and response are referred to as EDR.
Why is having a cybersecurity strategy important?
Trying to protect your organization from data breaches and security incidents without a cybersecurity strategy is like building a house without a building plan, it is quite a risky undertaking, to say the least. Businesses can no longer afford to approach their security challenge with a randomized array of tools and technologies; instead, they must adhere to a clearly defined cybersecurity strategy, especially in today’s digitalized environment where nearly half of all organizations lack an overall information security strategy. An effective cyber security incident response plan can benefit organizations by:
-
- Address their vulnerabilities.
- Protect their critical assets against intrusions.
- Invest in cyber security where it makes the biggest impact.
- progressively increase the maturity of their cyber security.
How to develop a cybersecurity strategy?
To develop an effective cybersecurity strategy, address several key questions first that will help structure and prioritize your efforts. Businesses must carefully consider:
-
- Which assets are crucial for my organization to protect and why?
- How can my cyber security strategy support my overall business objectives?
- Which security initiatives should be handled internally and which ones should be outsourced?
- Once your requirements, objectives, and capabilities have been established, it’s time to assess your present cyber security posture and consider how you might make it stronger over time.
What shift in cyber security is currently happening?
More than ever, companies are realizing that cyber security needs to be in line with broader business objectives because it has moved from being an IT issue to a business issue. A robust cybersecurity posture is necessary to ensure ongoing success, and more C-level executives and board members are ready to spend more funding on cybersecurity projects. Security professionals must be ready to present their cyber security strategy to the C-suite and the Board of Directors as decisions regarding the organization’s cyber security budget are frequently made at these levels.
What are the costs of our services?
Less than you might imagine and less than providing your protection. We have developed a method to offer small businesses enterprise-class cyber security at a reasonable cost. These costs cover everything, including our consulting services and managed security options for considerably less than it would cost to hire even one new security expert full-time. We can develop a monthly program that puts an entire team at your disposal, saving you both time and money.
Our 15 years of achievements includes:
-
10M+
lines of codes
-
2400+
projects completed
-
900+
satisfied clients
-
16+
countries served


